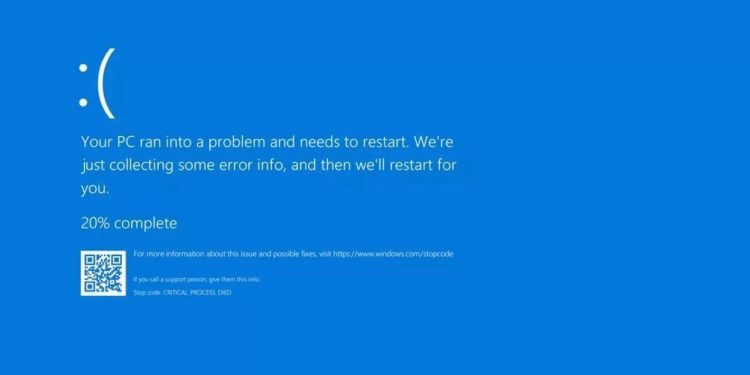
In a startling revelation, cybersecurity firm CrowdStrike disclosed that a bug in their endpoint protection software inadvertently caused disruptions to Debian and Rocky Linux systems. The flaw, which remained unnoticed for several months, has raised concerns over the reliability and oversight of cybersecurity solutions.
The issue came to light when a group of system administrators from various organizations began reporting unusual system behaviors, including random crashes and unresponsiveness. These symptoms were initially attributed to potential hardware failures or unrelated software bugs. However, a detailed investigation traced the root cause back to CrowdStrike’s Falcon agent.
CrowdStrike’s Falcon agent is widely used for its advanced threat detection and response capabilities. However, a recent update introduced a bug that interfered with critical system functions on Debian and Rocky Linux distributions. The bug primarily affected the kernel, causing unexpected system calls and resource management issues. This led to instability and performance degradation, particularly under heavy workloads.

The impact was significant but went unnoticed for months due to the sporadic nature of the disruptions. Affected systems included servers in data centers, enterprise workstations, and personal devices. CrowdStrike has since issued a patch to address the bug and has worked closely with affected organizations to mitigate the damage.
A spokesperson from CrowdStrike commented, “We deeply regret the inconvenience caused by this issue. Our priority is to ensure our customers’ systems are secure and stable. We have implemented additional safeguards to prevent similar occurrences in the future.”
The incident has sparked a debate within the open-source and cybersecurity communities. Critics argue that reliance on third-party security solutions can introduce unexpected vulnerabilities, while proponents emphasize the necessity of robust endpoint protection.
Debian and Rocky Linux maintainers have acknowledged the incident, highlighting the importance of comprehensive testing and collaboration with security vendors. They have also urged users to apply the latest updates and patches to minimize risks.

This incident underscores the complexity of maintaining secure and stable computing environments. It serves as a reminder of the delicate balance between security and system performance, and the need for vigilant monitoring and rapid response to emerging issues.
As the cybersecurity landscape continues to evolve, collaboration between software vendors, security firms, and the open-source community will be crucial in preventing and addressing such disruptions.